The persistent shortage of skilled cybersecurity professionals which grew by 26.2% over the past year, coupled with the fact that global cyberattacks increased 38% in 2022, means organizations are increasingly looking to security automation to help the cybersecurity teams keep pace.
In fact, 98% of respondents to our “2022 State of Cybersecurity Automation Adoption” survey say they have increased their automation budgets. This is great news for overworked analysts, but with that increased investment comes increased scrutiny of how that budget is being spent and the expected return on investment (ROI). Security professionals need to be armed with analysis to show the benefits and justify investments. ThreatQuotient can help.
A use-case based approach to ROI analysis
ThreatQuotient recently completed a use-case based approach to ROI analysis to quantify the value our clients are realizing with the ThreatQ Platform. One of the key benefits of the ThreatQ Platform is enabling “balanced automation” where repetitive, low-risk, time-consuming tasks are automated, while human analysts take the lead on irregular, high-impact, time-sensitive investigations with automation simplifying some of the work. Our analysis focused on identifying prime tasks well-suited for automation and quantifying the time savings to security teams when those areas are automated.
The following table summarizes the annual savings for each use case:
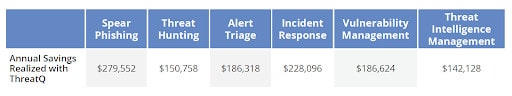
The calculations are based on industry research, plus experience working with multiple clients. Each use case provided enough savings to produce a positive ROI and short payback period after factoring in the cost of a ThreatQ license.
So how did we arrive at these numbers? Previously, we dug deep into two use cases: Spear Phishing and Alert Triage. Here, we’ll look at the remaining use cases.
ROI Calculation Snapshots
Threat Hunting: There are several challenges to threat hunting. Many security teams don’t know where to begin because they lack the ability to prioritize threats in their environment, and threat hunting requires specific skills, knowledge and expertise which few analysts possess. Once analysts do gain access to the data they need, they typically have no way to quickly connect the dots to understand the attack and the threat actor’s behavior. Organizations end up with high value resources spending inordinate amounts of time coordinating efforts and determining the best actions to take after the hunt to mitigate risk.
The ThreatQ Platform simplifies and accelerates the processes of hypothesizing, hunting and acting with capabilities including automated prioritization of data to support hypothesis development, support for collaborative investigations via ThreatQ Investigations, and the ability to automate response through ThreatQ TDR Orchestrator. This translates into a time savings of more than 1,200 hours for an organization with a single headcount focused on threat hunting. At a fully loaded hourly rate of $120 and the efficiency gains expected, we calculated an annual savings of nearly $151,000 from the threat hunting use case alone.
Incident Response: Gathering all the required information to understand the scope, impact and the actions required to mitigate damage post attack and recover is a difficult and often manual process, as data comes in a great variety of formats from many different teams and tools. If an incident under investigation can be related to a known campaign or adversary, the analysis and response time can be drastically reduced, since key tactics, techniques and procedures (TTPs) are already documented providing the proverbial breadcrumbs that lead to hiding places to look. But often there is no central repository for this data, or easy way to work collaboratively to accelerate investigation and response.
ThreatQ provides capabilities that accelerate tasks including creating defensive procedures, maintaining awareness of TTPs, conducting malware analysis, updating signatures, linking activity to known adversaries, stopping intruder access, and monitoring for changes in TTPs. Using the fully loaded hourly rate for an analyst responsible for incident response and an annual time savings of nearly 2,000 hours, the client was able to realize annual savings of nearly $230,0000 across the team responsible for incident response.
Vulnerability Prioritization: Even for mature organizations it is simply impossible to patch and mitigate every vulnerability present in an enterprise network, leading teams to prioritize mitigation based on limited and inward-facing data. Since a vulnerability is only as bad as the threat exploiting it and the impact on the organization, security teams must take a data-driven approach to prioritizing vulnerabilities based on this knowledge.
ThreatQ enables security teams to focus their vulnerability management resources where the risk is greatest by determining relevance to the organization and prioritizing on that; mapping to adversaries that target the organization with CVEs they use and other historical data; and continuously reassessing and reprioritizing as external and internal data evolves. Clients have reported efficiency gains as high as 90% when using the ThreatQ Platform for vulnerability prioritization, resulting in a savings of more than $186,000.
Threat Intelligence Management: Analysts are bombarded with millions of threat data points every day from multiple sources in multiple formats. They need a way to automatically ingest, consolidate, normalize and de-duplicate threat intelligence data from external sources in one manageable location. There’s also tremendous value to be gained from internal threat and event data for additional context, so that must be aggregated and stored as well. The next step is to correlate and prioritize all this data. But since what is a priority to one company may not be relevant to another, analysts need to control how scoring, prioritization and expiration are done. What’s more, as new data and context is learned, threat intelligence needs to be scored and re-scored so that reports and trending analysis is always up to date.
ThreatQ automates these processes to deliver significant efficiency gains. Clients have reported time savings of nearly 1,200 hours per year related to report generation and trending alone, realizing annual savings of more than $140,000.
You can see all the information here.