Escrito por: Kirsten Gantenbein, Principal Technical Writer, ExtraHop
ICMP is a network-level protocol that provides information about network transmission issues. For example, when an IP packet is unable to reach its destination, a router sends an ICMP message about the issue—such as unreachable network destination or time exceeded—to the packet's original sender. ICMP also offers a ping utility that can confirm healthy network connections. Except for ping and route tracing tools, users rarely interact with ICMP.
But ICMP is more than a diagnostic protocol. ICMP is also capable of shuttling data between two systems. Unfortunately, this makes ICMP an appealing vector for attacks that can secretly transport commands and exfiltrate data through ICMP tunneling.
Learn how ICMP tunneling works, how to detect ICMP tunneling, and how to prevent these types of attacks.
ICMP tunneling is a command-and-control (C2) attack technique that secretly passes malicious traffic through perimeter defenses. Malicious data passing through the tunnel is hidden within normal-looking ICMP echo requests and echo responses.
Let's say a user downloaded malware or an attacker exploited a vulnerability to install malware on a victim device. The malware must establish a C2 tunnel from inside the network to communicate with the external attacker. ICMP is a trusted protocol that helps administrators, so ICMP messages are often allowed to travel across firewalls and network segments that typically block inbound and outbound malicious traffic.
Different types of malicious data can be inserted into an ICMP datagram, from small amounts of code to a large encapsulated HTTP, TCP, or SSH packet. A datagram is similar to a packet, but datagrams do not require an established connection or confirmation that the transmission was received (unlike connection-based protocols like TCP). ICMP datagrams include a data section that can carry a payload of any size (see RFC 792). For example, if the attacker wants to create an SSH reverse shell (which enables the remote attacker to interact with the victim), the attacker can insert an SSH packet into the data section of the ICMP datagram that will establish the reverse shell. Or a compromised device can insert small pieces of exfiltrated data into the datagram of an echo request.
Over time, several ICMP echo request and response messages are sent between the compromised device and the attacker-controlled C2 server to exchange unique payloads of commands or exfiltrated data within each ICMP echo message.
But there are disadvantages to this technique. Some operating systems require root or local administrator privileges to create custom ICMP datagrams, and these privileges can be difficult for an attacker to acquire. In addition, ICMP tunneling through stateful firewalls or network address translation (NAT) routers also present challenges, because these devices filter ICMP echo responses that don't have a matching echo request. In these cases, ICMP tunneling might not be as reliable as other protocol tunneling methods.
Tools like icmptunnel can provide workarounds and simplify the process for creating an ICMP tunnel that encapsulates any type of IP traffic.
Monitor network traffic for unusually large volumes of ICMP traffic and non-standard or unusual ICMP datagram sizes. Legitimate ICMP echo requests and responses have matching identifiers and payloads that are a fixed or standard size, such as 64 bytes. For example, when a server receives an echo request, the server simply copies the 64-byte payload from the request and adds that same payload to the echo response. A network device that sends ICMP messages with unusually large payloads or sends more ICMP messages than usual might indicate tunneling traffic.
ICMP tunnel traffic can be difficult to detect. Software might legitimately verify healthy network connections with echo messages that have unusual payloads. To verify whether the payload has malicious content, unencrypted payloads in ICMP messages can be examined more closely with tools like Wireshark. Note that an attacker can still encrypt ICMP payloads to evade detection.
ExtraHop Reveal(x) automatically detects ICMP tunneling behavior by identifying unusual numbers of ICMP requests sent by a device over time, with each request containing a unique payload. Normal ICMP requests typically include a static payload that is repeated in multiple requests.
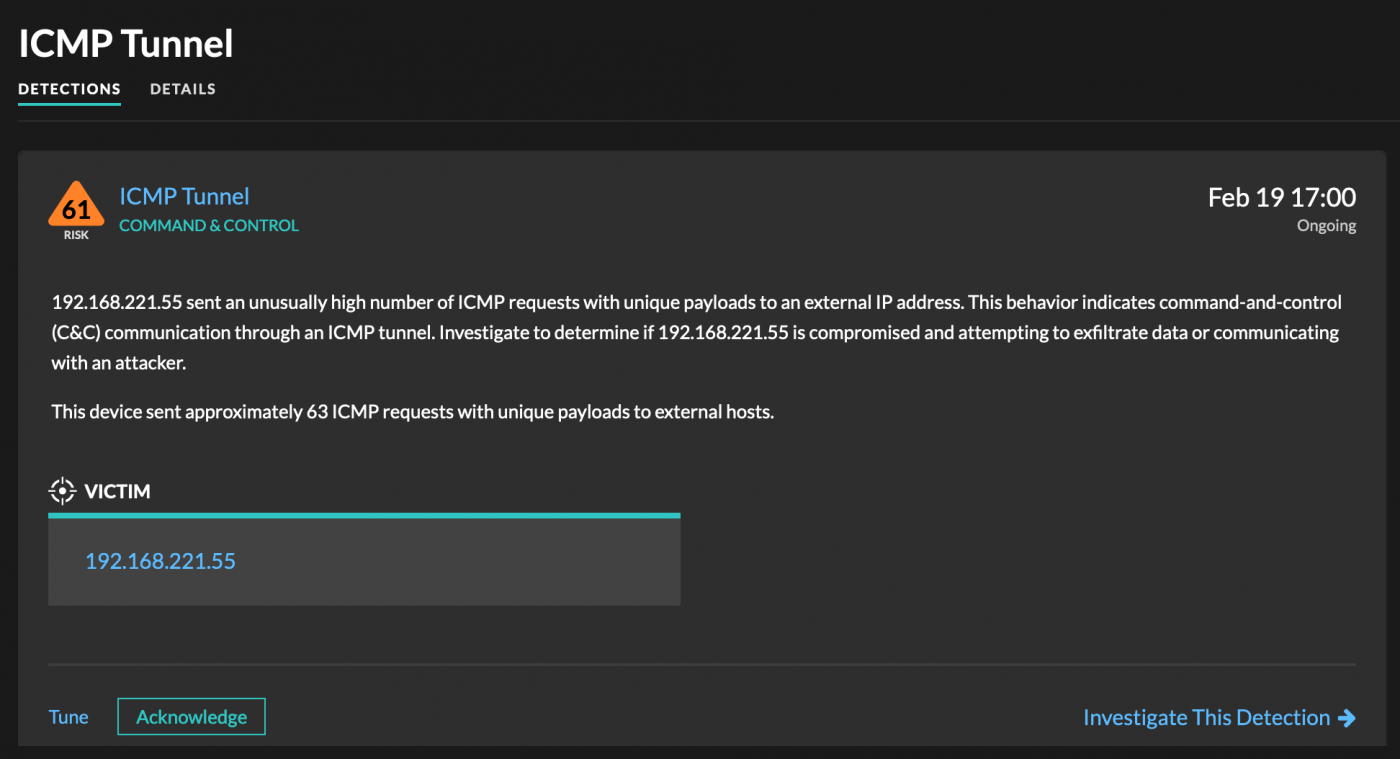
A defender can investigate the transactions associated with the victim device to determine whether a device communicated with a suspicious external endpoint. You can also determine whether network traffic for ICMP messages should be leaving the network.
Because ICMP helps maintain healthy network connections, blocking all ICMP traffic can create challenges.Known malicious endpoints and domains discovered through threat intelligence can be blocked at the perimeter. You can also configure firewalls to block outbound pings to external endpoints and only allow fixed-sized ICMP packets to pass through firewalls.
You can read the original article in ExtraHop website.