The pharmaceutical industry gained significant attention with the outbreak of the coronavirus (COVID-19) crisis. At the onset of the pandemic, demand from the pharmaceutical industry increased due to the need for COVID-19 treatment medication and prevention kits. The pharmaceutical industry endured a major shift in the threat landscape compared to the early stages of the pandemic from March 2020 to September 2021. Advanced Persistent Threat (APT) groups and cyber criminals targeted pharmaceutical companies to steal highly sensitive information, such as drug formulas and COVID-19 research and development data, which are extremely valuable to cyber criminals for financial gain, nation-state-backed actors to support their political agenda, and hacktivists to support their cause of economic or social awareness.
Recommendations
- Utilize account permissions best practices such as role-based access control, least privilege, and restricting root/admin permissions.
- Limit file egress by size and type.
- Disable macros whenever possible.
- Avoid opening unsolicited attachments and never click suspicious links.
- Enforce best practices on passwords, such as complexity, forced expiration, and prohibiting password reuse.
- Do not share passwords, and do not reuse the same password on different websites and applications.
- Log and monitor all administrative actions as much as possible. Alert on any suspicious activity.
- Consider disabling, or at least logging, all network activity outside of normal business hours for most users where possible.
- Disable unused ports on Internet-facing devices.
- Disable port echoing on all Internet-facing devices
- Use a VPN for internal network connections.
- If a workstation is infected with malware, quarantine it on a private network segment with no external connections.
- If you are alerted or suspect a compromised account, change the password immediately.
- Segment critical network resources using zero-trust configurations.
- Maintain regularly scheduled backup routines, including off-site storage and integrity checks.
Details
According to publicly available reports, a large percentage of the workforce shifted to remote working locations in the pandemic to follow COVID-19 health and safety guidelines. This provided the threat actors with a wider attack surface due to a dispersed workforce. During this time, phishing attacks were the most common vector to conduct malicious activity. To support staff working from home, organizations deployed remote working systems and networks — threat actors subsequently leveraged critical security vulnerabilities and stole sensitive information to fulfill their motives.
Based on this surge, the United States (U.S.) government quickly released a joint alert from the United States Department of Homeland Security (DHS), Cybersecurity and Infrastructure Security Agency (CISA), and the United Kingdom’s National Cyber Security Centre (NCSC).
Attackers most commonly employed phishing, malware distribution, and the use of typo-squatting domain attack techniques. The malware associated with some pharmaceutical-themed attacks included Agent Tesla (a keylogger malware), Get2 loader malware (Get2 loader has been observed loading the GraceWire Trojan), and TrickBot malware.
Some examples of reported attacks included ransomware attacks on a pharmaceutical company and biotechnology firm, and an attempted attack on the World Health Organization (WHO).
In the second quarter of 2020, cyber criminals targeted medical research organizations by luring victims with spear phishing techniques using COVID-19-themed malicious attachments. In one instance, APT32, a Vietnam-based threat actor group, targeted the Chinese government to steal COVID-19 treatment-related research with the METALJACK malware. At the same time, CISA, along with the National Security Agency (NSA) and cybersecurity authorities in the U.K. and Canada, attributed an attack to APT29 (also known as Cozy Bear) for targeting COVID-19 research and vaccine development facilities with cyber threats, such as a custom remote access trojan (RAT) known as WellMess and WellMail. The technique in the initial infection used mass scanning of vulnerable systems and then exploited critical vulnerabilities. APT29 was successful in using published exploits for products like Citrix, Pulse Secure, FortiGate, Zimbra to gain initial access in the organization. Moderna, a biotechnology company, also fell victim to a cyberattack conducted by China-based threat actors.
Some pharmaceutical companies that publicly disclosed their efforts in vaccine research and development became new targets for attackers. For example, pharmaceutical company LUPIN reported a cybersecurity breach immediately following the release of the Favipiravir drug used to treat mild to moderate cases of COVID-19. Although LUPIN was not directly involved with vaccination manufacturing, the launch of Favipiravir may have motivated threat actors to target the company for vaccine information.
Other examples of pharmaceutical companies — and companies working closely with pharmaceutical companies — exhibiting COVID-19-themed cyber threats include the following:
- India-based pharmaceutical company, Dr. Reddy’s Laboratories, fell victim to a ransomware attack in October 2020 after receiving approval to conduct phase 2/3 trials in India of Sputnik V, a COVID-19 vaccine developed by a Russian research institute. The company temporarily shut down several production facilities and isolated all data centers. In addition, it closed plants in the U.S., U.K., Brazil, India, and Russia.
- U.S.-based temperature-controlled warehousing operator and transportation company Americold, suffered a ransomware attack in late 2020, as the company had been in talks to store and transport COVID-19 vaccines.
- In December 2020, the European Medicines Agency (EMA) faced a data breach where documents relating to the Pfizer/BioNTech vaccine had been unlawfully accessed.
- The North Korea-based threat actor group, Lazarus Group, targeted a pharmaceutical company, as well as a government health ministry, dealing with the COVID-19 response with the mere objective of intellectual property theft. Suspected North Korean threat actors targeted AstraZeneca, a known COVID-19 vaccine manufacturer.
In the fourth quarter of 2020, after observing and analyzing the scope of cyber attacks on pharmaceutical companies, many cybersecurity companies released advisories, reports, and guidelines to protect valuable healthcare assets. However, compared to previous quarters, there were minimal publicly disclosed cyber attacks targeting pharmaceutical organizations for COVID-19-related data in the third quarter of 2021. Instead, there was a surge in mobile phishing and malware attacks due to increased use of personal mobile devices and bring-your-own-device (BYOD) for work. In the pharmaceutical industry, mobile devices are used across the entire supply chain, and proprietary data is stored in cloud services with the help of these mobile devices. Attackers that use social engineering techniques can easily compromise these devices. In these attacks, cyber criminals most often deliver malware like Monokle, SilkBean, and Wroba trojan. All three types of malware are Android surveillanceware containing comprehensive RAT functionality, including:
- Keylogging
- Taking photos and videos
- Retrieving application history from web browsers, social media services, and instant messengers
- Location tracking
With the second wave of the pandemic in 2021, Chinese threat actor group APT10 (also known as Stone Panda) identified gaps and vulnerabilities in the IT infrastructure and supply chain software of Bharat Biotech and the Serum Institute of India (SII). Both companies were involved in COVID-19 vaccination development and manufacturing. Security researchers assess that the motivation for the threat was to steal intellectual data related to the COVID-19 vaccine for a competitive advantage, as well as financial gain.
Pharmaceutical Industry Attack Surface Breakdown
Due to new COVID-19 health and safety guidelines, such as social distancing and remote working environments, many businesses relied heavily on internet-connected devices to facilitate business operations. However, this widened the attack surface for potential threats to businesses including the pharmaceutical industry. In remote working scenarios, commonly targeted assets and applications were interconnected devices running on the cloud, health information exchanges with third parties, and publicly-exposed systems.
The common MITRE ATT&CK framework tactics, techniques and procedures used by threat actors were:
Enterprise:
- Initial Access (TA0001): Phishing (T1566) – Spear-phishing Spear Phishing Attachment (T1566.001), Spear Phishing Link (T1566.002)
- Execution (TA0002): User Execution (T1204)
- Defense Evasion (TA0005): Regsvr32 (T1218.010)
- Lateral Movement (TA0008): Remote Services (T1021) – Remote Desktop Protocol (T1021.001)
Mobile:
- Command and Control (TA0037): Standard Cryptographic Protocol (T1521)
Due to increased development of linked Operational Technology systems and devices, traditional security methods were unable to secure the extended attack surface. This caused challenges for the pharmaceutical industry during the pandemic that included:
- Counterfeit and drug diversion in developing countries.
- Technology and network collaboration for safe vaccine distribution.
- Upgrade older technology systems to accommodate new security frameworks.
- Illegal vaccine distribution, including selling fake vaccines at higher prices.
- Cyber criminals spreading misinformation about vaccine safety.
- Vulnerable open ports with remote desktop and administrative tools affected supply chain companies.
- Insufficient email security lacking basic DNS-based email security protocols.
Pharmaceutical Threat Landscape Trend Analysis
Cyber criminals typically create attacks based on current events and topics that gain their target’s interest. The urgent demand for the pharmaceutical and medical industries to cope with the COVID-19 pandemic lured cyber criminals to target organizations within this industry vertical.
Some cyber criminals collected information against pharmaceutical companies and research organizations to get as much valuable data as possible to attack their specific targets or to engage in fraudulent activities etc. Coronavirus-related information was of immense importance for the nation state actors in the second quarter of 2020 when the pandemic started as this information needed to get ahead in the global race of vaccine research and development. After a period in which threat actors were particularly interested in COVID-19 data, cybercriminals moved their attention to companies who work with the government on vaccine development and distribution. The attackers now intended to disrupt vaccine production and distribution by attacking pharmaceutical companies, prompting them to shut down operations and supply chain companies to miss deadlines on vaccine deliveries. This would result in financial loss and reputational damage to the companies, revealing that the attackers were clearly monitoring the activities of the pharmaceutical companies and carefully picking their targets.
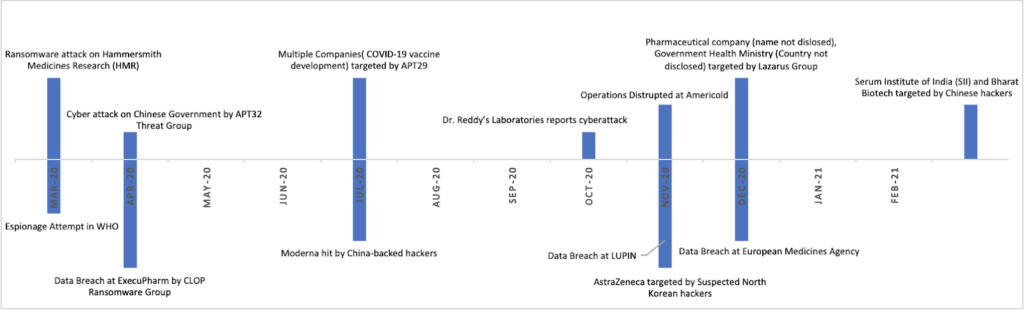
From the timeline in Figure 1, it is clear that pharmaceutical companies were targeted based on their role and involvement in COVID-19 response between March 2020 to March 2021. The cyber attacks on this industry will continue to be a susceptible target for the foreseeable future as a new COVID-19 variant, Omicron, has affected many individuals. Threat actors have already deployed phishing scams using an Omicron variant theme.
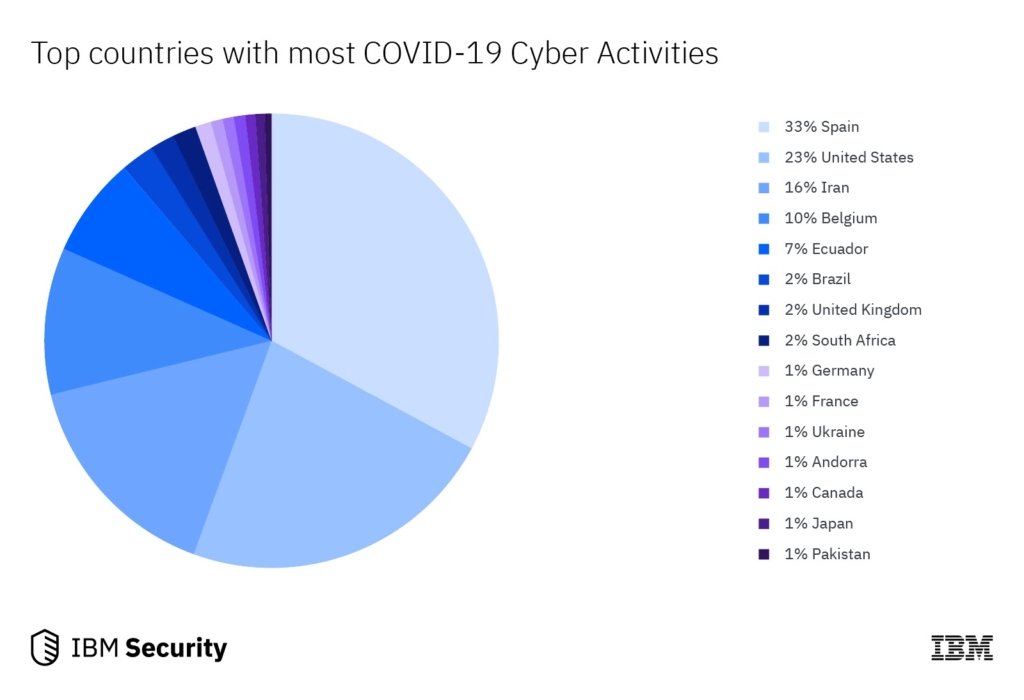
According to a report published by IBM’s X-Force research group in 2020, countries with a greater COVID-19 outbreak tended to have increased malicious activities related to COVID-19 threats.
Impact on COVID19 Supply chain
When COVID-19 vaccines were manufactured after the trials, attackers were quick to understand that the supply chain sector would be an ideal target for cyber attacks, due to dependency on mobile devices for inventory and communications in this sector. During this time, organizations followed COVID-19 health and safety guidelines by having a limited onsite staff perform operations to maintain social distancing. Therefore, it was easier for a remote attacker to gain entry into the system by physical and virtual means as not many staff are monitoring the assets and operations of the organization.
With the rise of teleworking infrastructure, threat actors used social engineering techniques to exploit vulnerabilities in remote working tools and software by targeting users with various types of phishing such as SMS-based phishing, credential theft, and phishing emails to distribute malware.
With financial-gain motivating threat actors, observations indicate that some APT groups were more interested in stealing COVID-19 research for a geopolitical advantage, as the information could be useful for domestic research into COVID-19 treatment. Although COVID-19-themed cyber attacks started in the beginning of 2020, the attack on supply chains emerged in the middle of the same year. It is notable that a delay in the distribution of vaccines could lead to the spread of more COVID-19 infections. In addition, the third party vendors remotely delivered their services to healthcare organizations which also increased the attack surface due to remote working environments.
Conclusion
Based on ZeroFox analyses, it is clear that cyber criminals primarily targeted pharmaceutical companies’ sensitive data for financial gain, one of which was through ransomware attacks where operators demanded a ransom payment in exchange for stolen data. Then, they focused on research related data that could lead to business loss and ultimately financial loss for the organization. Companies in the pharmaceutical industry cannot afford to lose valuable data, access to critical systems, or disruptions in their operations, especially during the pandemic. This situation requires an immediate incident response plan to deal with any kind of cyberattack on a real time basis. The increasing rate of cyberattacks is becoming a major risk to public safety and national security due to a wider attack surface. Based on these observations, it is speculated that the pharmaceutical industry will continue to be on the target list of the attackers and could be hit with cyber attacks in the future.
For more information please click here.

